 Warning: the NAG-like notation used on this page is not exact but gives the flavor of the notation.
Warning: the NAG-like notation used on this page is not exact but gives the flavor of the notation.
 Warning: the NAG-like notation used on this page is not exact but gives the flavor of the notation.
Warning: the NAG-like notation used on this page is not exact but gives the flavor of the notation.
Say you have this portion of an audit graph:
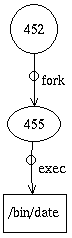
which is represented like this in the NAG file:
(Node A; Physical: {shape=circle,label=452},
Audit: {pid=452,auid=smith,ruid=...})
(Edge 1; Physical: {src=A,dest=B,label="fork"},
Audit: {event="fork(2)"})
(Node B; Physical: {shape=ellipse,label=455},
Audit: {pid=455,auid=smith,ruid=...})
(Edge 2; Physical: {src=B,dest=C,label="exec"},
Audit: {event="exec(2)"})
(Node C; Physical: {shape=box,label="/bin/date"},
Audit: {file="/bin/date",filemode=755,...})
And you want to to change it to look like this:
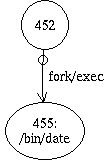
which is represented like this in the NAG file:
(Node A; Physical: {shape=circle,label=452},
Audit: {pid=452,auid=smith,ruid=...})
(Edge 1; Physical: {src=A,dest=B,label="fork/exec"},
Audit: {event=("fork(2)","exec(2)")})
(Node B; Physical: {shape=ellipse,label="455:/bin/date"},
Audit: {pid=455,auid=smith,file="/bin/date",filemode=755,ruid=...})
This transformation effectively combines of the the typical fork and exec pattern that is seen in audit graphs when a shell command is executed and reduces the number of objects by 2 without losing any information.The english equivalent of the rewrite specification for such a graph would be:
--
Find a node x
Find a node y
Find an edge e with physical attributes src=x and dest=y and with audit attribute event="fork(2)".
Find a node z with with file != "".
Find an edge f with phyical attributes src=y and dest=z and with audit attribute event="exec(2)".
--
Change edge e's physical attribute "label" to "fork/exec" and audit attribute "event" to the list {fork(2),exec(2)}.
Add node z's audit attributes to node y's.
Change node y's label to be it's audit attribute "pid" then ":" then z's audit attribute "file".
Delete node z and edge f.
--
Another transformation that you might want to make is to remove all the objects replated to "ioctl"'s and dynamically loaded files since they possess little useful information (not shown).


 Last revised 12-Oct-94 by Jim Hoagland
Last revised 12-Oct-94 by Jim Hoagland