GLOBAL GUARD MEETING
December 8, 1998
3085 ENG II
3:15-5:00 p.m.
In attendance:
Karl Levitt (KL), David Klotz (DK), David O'Brien (DOB), Jeff Rowe
(JR) and Steven Templeton (ST)
TOPICS
Global Guard Presentation at DARPA PI Meeting
Scenarios
-
Global Guard Presentation at DARPA PI Meeting
-
Scenarios – demonstrate kinds of correlations
-
Root cause
-
Put attack pieces together (Aggregation)
-
Synthesis (putting things together) and Analysis (breaking things down)
-
Scenario #1: Jeff’s scenario

-
Scenario #2: Aggregation – missing link

-
Scenario #3: Look at normal data to determine statistics of normal network
activity
-
ST: Generate a graph from activity on network
-
ST: Find a commonality; then determine non-normal activity

-
Need a big data structure that’s efficient and statistical information
on selected features
-
JR: Profile applications based on activity on network
-
ST: Process as you go, create summaries, incremental
-
KL: Can GrIDS help us generate the rules automatically?
-
JR: Through a model of causality and Yemini’s rules, you can infer rules
-
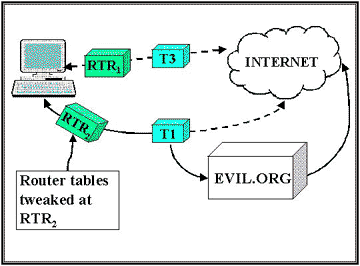
Scenario #4: Weak symptoms, missing data – Router broken into:
-
Moved to T1 Backup
-
Trace route: Traffic goes through EVIL.ORG
-
RTR2 Audit Logs show Table Updated
-
Check RTR1, put in anti-DOS filter
-
Run IDIP, trace back to attacker
-
Can we infer what the root cause is?
-
Automated Response: enumerate all causes and responses
-
Function for response needs data function
-
IDIP codify into Yemini
-
Why do we care about the cause?
-
Find out the attack site
-
Inform our neighbors
-
Identify the service exploited and identify the capability of spreading
-
Identify the vulnerability to prevent it from happening again
-
Stop current attack



