BOEING MEETING
June 10, 1999
1-2 pm
3085 ENG II
In attendance:
Jeff Rowe (JR), Jason Schatz (JS), David Klotz (DK), Karl Levitt (KL),
Chris Wee (CW) and Erich Morisse (EM)
-
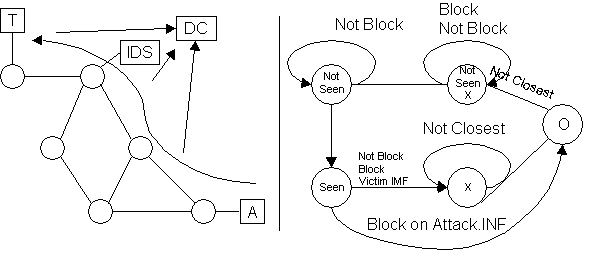
Revisit the Nearest Neighbor Model
-
CW: In anticipation of criticisms:
-
What is the utility of finding the closest router to an attacker? All leafnets
have firewalls
-
DK: This method doesn't address external attacks; only internal ones.
-
Why not block everywhere?
-
DK: Don't want to block everywhere adding useless work
-
What about blocking one connection or connectionless attacks? Not all attacks
come through TCP wrappers
-
DK: The argument is that given that blocking is good, this is one way to
do it.
-
If you have the capability to block the signature of a well-known attack,
why not just implement it?
-
JR: For attacks like port scans, you cannot block ahead of time
-
DK: Blocking a new attack is quick and effective with this method.
-
What is the point in installing filters after an attack?
-
List of strategies
-
Isolate Attacker
-
Isolate Target
-
Block All Paths
-
Isolate Cheapest Link in Attack Route
-
Isolate Infected Machines (Worm)
-
Block Everywhere (Worm)
-
Strategy to clean up machines after worm contained
-
Issues
-
Dealing with a distributed coordinated attacks
-
Treat attacks individually
-
Send identical attack packed from two locations
-
Reverse path poisoning - so routing protocols won't go crazy
-
How Discovery Coordinator will interface
-
Ultimate goal - measure against utility function
