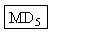 à
M1’
à
à
M1’
à 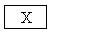 M2à
M2à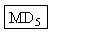 àM1’
àM1’
In attendance:
Tuomas Aura (TA), Brian Cameron (BC), Todd Herberlein (TH), Keith Herold
(KH), David O’Brien
Questions:
If you use the non-encryption option and use compression instead, is
that secure?
It is possible to break into the data stream
Will non-encryption be an option on future versions of SSH?
Non-encryption may not be available in Version 2.
In version 1, it is a flaw, because Version 1 depends on the client and
server to authenticate each other.
David O’Brien models CRC
M1 à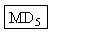 à
M1’
à
à
M1’
à 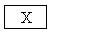 M2à
M2à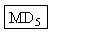 àM1’
àM1’
M1 à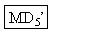 à
m’ à
m’ |
Possible in SSH |
M2 à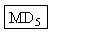 à
m’ à
m’ |
101110110111010 à CRC16à
X16bit
Change in one number should not allow same X
CRC only detects random errors
Root kit
 à
CRC à Xg
à
CRC à Xg
 à
CRC à Xe ¹
Xg
à
CRC à Xe ¹
Xg
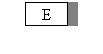 à
CRC à Xe’ = Xg
à
CRC à Xe’ = Xg
(Add extra
bit)
X-11 Forwarding