VULNERABILITIES MEETING
April 12, 1999
4:00 – 4:30pm
3085 ENG II
In attendance:
Matt Bishop (MB), Tuomas Aura (TA) and Todd Heberlein (TH)
-
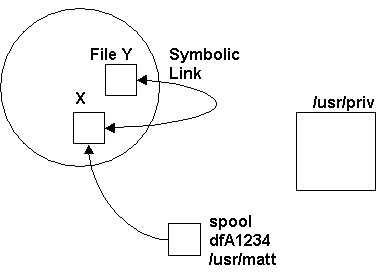
Symbolic Links
-
Indirect aliases - instead of pointing to an inode, it points to another
name or inode.
-
The goal is to formalize symbolic links to see whether eliminating or redefining
symbolic links reduces race conditions.
-
Issues
-
LPR is written
-
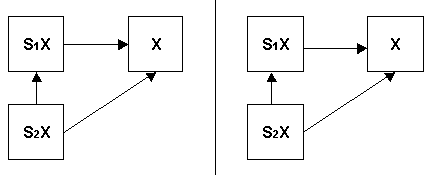
Symbolic Links vs. Hard Links
-
If treated as a hard link, would the vulnerabilities be different?
-
Cannot chain hard links
-
Symbolic Link - restricting length of chain
-
What happens if target doesn't exist?
-
Macintosh model - can't point to a pointer
-
Could introduce new symbolic link
-
Comments
-
TA: The link looks like any other name - is it a file or a name? Is there
a way to evaluate attributes?
-
MB: HPs and Iris symbolic links are different from DECs
-
The semantics are not well settled; they are inconsistent between systems.
-
Why would you change ownership of a symbolic link?
-
TA: You should not be allowed to check permission of a pointer to an inode
or the object itself
-
You need to resolve the name issue
-
Access to object, permissions, properties
-
Bind(fd, name)
-
Open (fd)
-
Secure bind - not follow any links?
-
Sbind (fd, name w/o links)
-
New API
-
3-4 attacks involving finger - which systems have which semantics
-
Are there similar problems in NT?
-
Macro language
-
Discuss Melissa virus at next Vulner meeting - it affected Window 98, 95,
NT and Macs.
-
IT teaches classes in macro language

